A trend of the past couple of years has been for scammers to contact computer owners directly via telephone in the United States in an effort to convince them that there is a problem with their PC and they’ll need to pay to have it fixed. In general, these people cannot fix anything, and instead they merely charge exorbitant fees for absolutely nothing. In other words, they scam you.
The call generally goes something like this:
- A foreigner with a thick Indian accent identifies himself as a member of Microsoft Support or similar.
- He informs you that you have a number of critical problems with your PC and that you will need to have it fixed.
- To convince you, he offers to connect remotely and pulls up your Event Log (eventvwr.msc). He then filters for Warnings, Errors, and Critical events and uses that as evidence that your PC will soon fail to work correctly if you do not pay him to correct it.
The astute among you have probably already sensed that something here is seriously wrong, and it’s not your PC. It’s the fact that someone is calling you to tell you there is a problem with your computer. No one will ever do that. The only way they could possibly know there is a problem is by hacking or guessing.
In this case, it’s mere guesswork, and it’s not even correct most of the time. The Event Log is supposed to log warnings and errors, and even on the healthiest of PCs there are plenty of Error Events that can be safely ignored, as they often don’t amount to anything. The important thing to remember is to never trust someone who calls you about a problem with your PC, and never, EVER let them connect remotely to your PC.
If you do make the mistake of letting them connect, but then you happen to get cold feet and refuse to pay the $180+ they request via credit card, the next thing that happens isn’t pretty. This scammer proceeded to actually follow through on his promise of the PC “not working” if they don’t agree to have him fix it, and so in a few quick steps, behind the user’s back, he enacted what is known as SysKey encryption on the SAM registry hive.
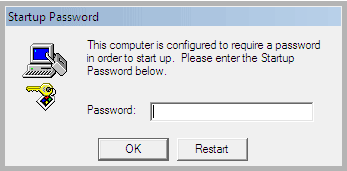
SysKey encryption is a little-known feature of Windows which allows administrators to lock out access to the Security Accounts Manager (SAM) registry hive so that login specifics cannot be stolen and the PC cannot be accessed without knowing the proper credentials. The problem is, unlike other scams, there is no way around the problem; you can’t simply remove the password, as the actual SAM hive has been encrypted entirely by the process. If your Windows installation has had SysKey activated, you’ll see the following message:
Startup Password
This computer is configured to require a password in order to start up. Please enter the Startup Password below.
The window which appears looks like this:
The ONLY solution is to find a clean copy of the registry hives from before this occurred. This scammer knew this, however, and as such, he took an extra step to block any repair or recovery attempts: he deleted all System Restore points on the machine, which normally house backup copies of the registry hives.
Unfortunately for him, I’m a much better technician. When the customer suspected foul play and decided to call me instead of proceeding, I immediately instructed them to power off the PC. Here’s how I fixed the problem without having to reinstall Windows.
FIRST, ensure you don’t have any Restore Points to work with:
- Check to ensure that the folder %SYSTEMROOT%\system32\config\RegBack exists. This is the folder which contains the last known good backup of the hives following a boot. If it exists, continue. If not, stop and consider contacting a technician instead.
- Reboot the PC and repeatedly press F8 to reach the Advanced Startup Options menu.
- Choose Repair your Computer from the menu.
- Cancel the automatic repair attempt and instead instruct the system to perform a System Restore to a date prior to the incident occurring.
If no Restore Points exist, your scammer intentionally removed them to prevent this from occurring. If this happens to you, follow these additional steps to resolve the problem:
- POWER OFF your PC immediately.
- Boot to external media of some sort (NOT your Windows installation) and navigate to the %SYSTEMROOT%\system32\config folder.
- Backup the registry hives in this folder to a temporary location. The files are:
- SOFTWARE
- SYSTEM
- SAM
- SECURITY
- DEFAULT
- Navigate to %SYSTEMROOT%\system32\config\RegBack as mentioned earlier.
- Copy all registry hives from this folder (the same files as listed above) into the %SYSTEMROOT%\system32\config folder.
- Reboot the PC.
This solution only works if you have not already tried to reboot the PC subsequently. If you have, it may still work, but that is entirely dependent upon whether or not Windows created a new RegBack copy following a successful boot.
In the case of my customer, it worked, and they were back in Windows, just like it never happened. Nice try, scammer. You’ll have to try harder to beat me though. 🙂
Addendum A (update 6/26/2015):
Thanks to FUScammers for pointing out this more involved, alternate method of actually removing the SAM encryption.
- Download this file and burn the .iso to a CD.
- Boot to the CD on the affected system.
- Follow the instructions to select the proper system drive and partition (NTFS is the partition type you are looking for).
- Type the path to the registry files (it’s most likely Windows/system32/config).
- Choose option 1 for Password reset (sam system security).
- Choose option 2 for Syskey status & change.
- Confirm that you wish to disable Syskey, then quit and confirm writing the new changes to the hive.
- Reboot the PC and check.
For more detailed instructions, check out this link (scroll down to “How to disable Syskey startup password”):
http://computernetworkingnotes.com/xp-tips-and-trick/remove-administrator-password.html
In Windows 8, the GPT partition type makes the use of this utility impossible. However, you can still manually copy the hives to a supported filesystem (NTFS or FAT32), mount that filesystem instead, and follow the steps from there, then copy the hives back over the originals. I can confirm that this method does work and that even in Windows 8.1 recovery is possible using it.

Thank you for taking the time to discuss this scam. I have read several complaints posted at http://www.callercenter.com but I didn’t think it’s this complicated. One thing I know for sure, though, is that Microsoft never initiates a call.
Thanks for this procedure! Fortunately, the RegBack files were intact and modified only a few days earlier. Booting into Linux, copying them back to the Config folder did the trick. After trying other measures, no other options were seemingly available. And YES, they trashed System restore.
This scam occurred on a friends computer; however, he was not clear on just how they gained access to his system after walking him through various menus, etc., while on the phone. I still wonder if they have access to the system.
No RegBack – I now assume a new Windows must be installed?
Even Renamed the SysKey.exe to SysKey.org – no difference. Still asks for a Password.
Hey Peter,
No restore points either?
Renaming will not work as the problem is encryption of the SAM registry hive itself, which is required to boot into Windows.
Thanks for posting your solution. My friend was also a victim of this scam. Fortunately, she did have RegBack and I followed your example and got her computer backup and running. Saved us valuable time from reinstall.
Thanks again.
Del
This scam just happened to a family member of mine. Should they be concerned about identity theft and such or is this just a scam to get a credit card number and mess up the computer?
Lisa,
Unfortunately, there is no way to know for certain. Such unscrupulous individuals are likely just after quick money, but who is to say that once they’ve gotten control of your system, they haven’t found a way to transfer data to themselves or otherwise steal information?
The best course of action is to change all passwords just to be safe. You can also alert your bank or credit card company to let them know to be on watch.
-Steve
Thanks Steve, I wish I had answered the phone instead of my trusting father. Fortunately i started to listen in on his conversation when he was about to give his credit card info. When we shut down the call they locked up the computer. I’m sure it will cost more to unlock and fix the computer then what these sleaze balls wanted to charge him.
Thanks so much. After much searching i found your solution and was able to get into the system. They did more damage but being able to get into the system was huge for me. I have transferred all my important items and did a full system restore to brand new and they just restored my files and all works great again. Only about 4 hours of my day wasted on this for a customer.
This is the 2nd time I have seen this, first time was able to system restore. This time however they had teamviewered into computer and wiped out system restore points. This solution worked perfectly as I had found the files in regback which were 8 days old. Followed instructions and it worked. Thank-you and my friend thanks you. And the guy in Italy is kinda upset (John Mensah) who wanted money.
i cant even access the deskop and it window 8 so no f8
what can i do
I’m a tech. These f***wits call me at least once a week, following which I usually suggest they carry out some rewarding physical exercise.
However, this time it was a customer who got scammed with the SysKey method, losing files in the process and being locked out of her computer. I’d never seen this level of attack before, and wasn’t sure how to handle it, so I first tried KonBoot, which usually takes you past the password entry point and into the system. (You can’t change the password but at least you can get into the system) However, this didn’t work with this attack.
Next I tried ERD Commander, both their old versions and the newer DaRT versions. No joy.
Finally got rid of the thing with Passware Windows Key Enterprise 9.3.815, which actually recognized the attack system. First I set a password for Admin and removed all others. After that I was able to enter the system (W7HP) and tidy up the User accounts. The customer had lost documents – apparently the sleazebags got pissy with her when she refused to pay and deleted a bunch of files. However, I’d backed them up a few weeks earlier so no prob there.
Couple of points to pass on to your friends: No matter what we think of Microsoft’s foibles, failings and f***ups, phoning customers like this is something they’d NEVER do. Also, there’s no way of accessing a computer system without the owner’s cooperation. So there’s NO WAY the caller can know if there are any bugs, errors or faults in the computer system, UNLESS they get invited in. Personally, I always turn off Remote Control (on by default) whenever I service a computer. Finally, all someone has to do if they’re beginning to smell an Indian rodent, is press and hold the power button (desk or laptop) for about 10 seconds and the machine will power off.
Good luck folks 🙂
Hello. I have a customer’s PC in my shop which experienced this. I am currently to the state where Windows boots normally and by appearance all looks normal. Except….the following programs are either disabled or missing the appropriate registry/service to operate:
1) Windows Update (it causes Dell’s update program to not work either)
2) Windows Defender
3) Windows Restore
I am sure that there are others that I have not noticed yet. I have run scans from malewarebytes to microsoft fix-it to Kaspersky. I ran others that I’m too tired to mention. I’ve run into this before and just rebuilt the PC. I’m not against it since I already have an image loaded to a disc for this model, but I’d really like to learn how to repair this for future knowledge.
Thanks in advance,
Brian
Hey Brian,
My very first thought with those symptoms is the ZeroAccess rootkit. Check to be sure the relevant services exist (you can start with these commands at the Command Prompt):
sc query MpsSvc
sc query bits
sc query wuauserv
sc query WinDefend
If any of the services are not installed, you will need to restore their functionality using the relevant registry keys for each service based on the OS version that’s installed. However, if MpsSvc and bits are missing, it’s probably the work of ZeroAccess.
On the other hand, I would also check to see if any NTFS junctions have been placed overtop the Windows Defender files in the Program Files folder. If so, it’s a surefire dead giveaway that this machine is infected with one of the latest variants of the ZeroAccess rootkit, which uses those junctions to block access to those files and prevent reinstallation of the security. It is sophisticated stuff as far as malware goes, though I remove it at least once per week these days!
Hope this helps!
PS– System Restore can also be broken if either (or both) VSS and WMI are corrupt. You can repair the Volume Shadow Copy Service (VSS) using utilities such as Windows Repair All-in-One and WMI using similar utilities. They’re a bit risky, but in situations like this where such deep damage has been done it’s a great place to turn. I personally use FoolishIT’s D7 for such repairs now, but it’s nowhere close to free. 🙂
Steve,
Thank you so much for taking the time to respond to me specifically. I did operate the run command to learn that all four services are available and their status was set at running.
I ran Windows Repair All-in-one (aware of the risks, that it okay because I cloned the original drive and I am working on the clone) to no avail. It appeared to be repairing quite a few services, but afterward (and after a restart) I am still at the same status as before.
I suppose I’m going to try some other rootkit options now. If I don’t find a solution by tonight I’m going to have to rebuild. This is a business computer and needs to be back into service soon.
Thanks for the help,
Brian
If you haven’t already, make sure to also run a chkdsk on the machine ( chkdsk /f %SYSTEMDRIVE% ) to ensure no filesystem corruption. Then, you can always try:
net stop wuauserv
net stop bits
ren %SYSTEMROOT%\SoftwareDistribution %SYSTEMROOT%\SoftwareDistribution.old
net start wuauserv
net start bits
And see if that corrects anything on the Windows Update side of things. However my guess is that you may still be looking at a WMI problem. There are various other ways to repair a corrupted WMI repository if it needs to be done… if you need help I can try!
From the Command prompt, I ran:
net stop wuauserv = this worked
net stop bits = the background intelligent transfer (bit) service is not started
ren %SYSTEMROOT%\SoftwareDistribution = The syntax of the command is incorrect.
A friend of mine has been a victim of this scam and I’m attempting to recover her files as there is no way in heck I am able to bypass the Startup password. My operating system is WIN XP Home Edition SP3 – I can’t boot to command prompt in safe mode because it asks for the password, it won’t boot to anything at all. How do i boot to an external media to access the %SYSTEMROOT%\system32\config folder?
Thanks,
Sean
Hey, just wondering if anyone is out there to help me with my issue posted above. Thanks!
Sean
Hey Sean,
Any other boot media works which can access the NTFS filesystem. Google ubuntu Live and try that as it is free.
Thank-you so much. I used this program and was able to access all the data which was thought to be lost. Great program… I may use it permanently 🙂
Thanks again Steve,
Sean
Pingback: Increase In Hacking Attempts » Tech Guru Squared
Thanks, worked like a charm.
Pingback: Windows 8 Boot problems after using chntpw utility | Ubuntu InfoUbuntu Info
Heyy Steve Schardein.. thanx for your suggestion, but I am unable to rectify this error on my windows 7 (Home edition) PC. i followed all of your steps, but it could not help me. i dont have any system restore point. please Help.
Thanks, just fixed a friends computer using the reg back up method. Worked a charm.
+1 internets for you sir.
Worked a treat (used hdd in another PC to copy in old reg files …. knew by date stamps that they were ok).
Thanks a lot.
Hello Steve,
Thank you for this explanation. I’ve also helped a customer on XP with this scammer problem and stumbled upon this page for help. He had turned the computer back on with no backup to speak of so there was a big problem.
I tried the Offline NT Password removal which removed the initial Startup Password screen but seem to damage the account passwords for all current users. I couldn’t even get in using the administrator account. I was able to finally add a new user for the customer to use via command line – using a command line backdoor. It was a lot of stuffing around.
I also used EaseUS Data Recovery which did a fantastic job at recovering the deleted files this scammer started deleting.
Microsoft should really disable Syskey for its Home editions of Windows – a very dangerous system program in the wrong hands. Still available in Windows 8 too.
Hi everyone!
First of all… I am by no means a tech. I like to think that I can get around a PC quite well for someone who doesn’t have any formal training. My uncle had this happen to his PC (Windows 8 – which I have only spent about 10 minutes on the system to-date). I haven’t read all of the comments yet but the first question that comes to mind is: how can I search for the registry folder if they can’t even get into windows (because of the ransomware asking for a password). Please note that I don’t have access to the PC as I live too far and I will be attempting to do this with them over the phone (they aren’t so tech-savvy). I’m hoping to avoid re-installing windows since I don’t think they received a recovery CD or anything with their laptop.
Any help would be greatly appreciated! 🙂
Steve,
This just happened to my father (exactly the way you described it above). Although they threatened that he would “never use his computer again” after he made the error of letting them on his computer via TeamViewer, I was able to go in (it’s Windows 8), change the computer password and get past the Startup password window that came up because, obviously, they activated SysKey. I uninstalled the TeamViewer program and everything seems to be okay. However, I tried to complete a System Restore and a window came up following the attempt that said that it could not be completed because, possibly, one of the drives might be corrupted. It recommended running “chkdsk /R” but I’m not sure how to do that. Are we at the point now where I need to have someone like yourself look at it? Are there any other options I can try in order to complete a System Restore? Should I just reset everything to the default settings (my father has only had the laptop for a few months)? Any help or guidance would be GREATLY appreciated. Thanks.
Hey Vanessa,
Sorry–there is literally no way to do this without physical access to the PC! The best option in this case is certainly to reformat. If there is no CD with the Windows installation you might need to contact the manufacturer about this (I know it’s not what you want to hear :)).
Jeremy,
Same goes for you too… it sounds like you may have multiple issues on your hands, but it’s unclear. It may also be infected, or it could actually be a storage device failure. Either way, your safest bet, especially if everything is already backed up, is simply to start from scratch. Or, of course, bring it to a good tech!
Pingback: ALERT: Fake "Microsoft Support" Telephone Scam - BCCS Computer Systems :: BCCS Computer Systems
Thank you very much! Worked for me on a Windows 8 laptop which had been started and switched off dozens of times since the problem first occurred, which means that the backups of the registry hives must occur later in the startup than the point at which the system prompts for the syskey password. I used a copy of Microsoft’s DART utilities to run a command prompt on the affected machine and backed up the old files and copied the backups into their place. I was unable to run ANY local recovery tools as without access to the SAM, none of the tools could detect a local administrator account.
Hey Guys,
I had a call from a client tonight who’d been called by “Windows Best Help” Who gained access to the clients machine and installed rubbish “clean up tools” and charged them $200.
If you’re like me – you want these filthy creatures to rot in hell.
Fortunately my client called me and we were able to kick them out of the system before anything bad happen. Last week I had a client who had their registry SAM file encrypted and password protected by these scammers just like in this article.
ANYWAY – I got their 1800 phone number and have been calling them non-stop all night in order to tie up their phone line. This is a simple way to help prevent others getting scammed and it’s frustrating the hell out of them!
If you want to join me in this mission, then call them on 1800 427 765 and WASTE as much time of theirs as possible.
Be careful not to call from your mobile (As you’ll get charged) and they’ll get your number.
I call from Skype, which shows up as private for them and doesn’t cost a cent.
I’ve spoken to them over 20 times and had all sorts of fun. They are no longer answering but know that this also stops legitimate victims from getting scammed.
Also remember, as it’s a 1800 number, they pay every time they answer. It’s pure gold!
I’ve also recorded all the calls and did a screen recording and have some really funny recordings – let me know if you want me to post them.
Cheers
Richard
Excellent! I am definitely donating month end!
Hi – – My girlfriend fell for this scam. She has winxp pro on her computer.
I haven’t used xp in a while, so I’m stuck.
How can I get into system restore (her restore points are still there), if I can’t get into any safe mode, or recovery console (even that asks for a password)?
Or if I put her hard disk into my computer, is there a way to do a system restore to that disk? Any help. or links would be appreciated… thanks!
By the way, in xp there is no “Repair your Computer” option in advanced startup options, otherwise it’d be fixed by now… thanks!
Hey baz,
Well, for starters, I’m assuming you already are aware that her running XP is a HUGE security risk in and of itself. It is going to be a veritable hotbed for malware going forward now that Microsoft has finally officially revoked support for it. So it may not be a bad idea in this case to simply wash your hands of it all, boot to another OS/slave the drive to another machine, back up the user data, and reinstall 7 or 8.
Having said that, to get her back in, it’s a little trickier on XP. Here is a post I made a while back on the subject:
http://triplescomputers.com/blog/casestudies/when-last-known-good-configuration-fails/
(see the XP paragraph)
If the RP folders are missing, the attacker deleted the RPs. In that case, you can try C:\Windows\restore and see if the hives are there, but if they are, they are likely VERY early versions of them. So it’s not a good solution.
By the way, LKGC won’t work here anyway. The SAM hive is not included as a part of that recovery operation; the system merely switches the CurrentControlSet to a different number in that case instead. This is all, of course, to avoid subversion by an attacker should an admin ever enact SysAdmin encryption. It is not *meant* to be subverted.
Good luck–if those RPs don’t exist, you’re probably SOL on this one!
Steve
I’m just posting this as an additional solution for anyone who has this problem in the future and finds this topic:
I recently encountered this problem and found that the password needed to get into Windows was 123. I’ve read others that had 1234 or 12345 as their passwords. So before going to great lengths booting into Ubuntu and trying to mess with Registry files from there, simply try those three passwords.
If the password works, you will get back into Windows, but you will still have the password prompt popping up every time you re-start Windows. To disable the password prompt I followed the steps here: http://www.sevenforums.com/tutorials/243880-syskey-set-startup-password-lock-unlock-windows.html (Before doing this procedure, I tried a few different system restore points, and although they each finished the restore process, I got an error once booting back into Windows, saying the restore failed, and the password prompt kept popping up. There was also no Regback folder to be found.)
Additionally, once getting back into Windows and disabling the password prompt, you should run scans with the following programs to clean up leftovers from the scammers:
ADWCleaner download here: http://www.bleepingcomputer.com/download/adwcleaner/
aswMBR download here: http://www.bleepingcomputer.com/download/aswmbr/
TDSSKiller download here: http://www.bleepingcomputer.com/download/tdsskiller/
Malware Bytes Anti Malware download here: https://www.malwarebytes.org/free/
Avast Anti-Virus download here: http://www.avast.com/index
http://www.youtube.com/watch?v=5ow0NCpD0bU
Pingback: The Easiest Way To Tell If The Windows 8.1 Update Is Installed On Your Computer | What's On My PC
thank you so much this worked flawlessly :DD
Just recieved a clients notebook with Win 8.1, who also chatted with this Indian crooks… this installation is totally toast! Their normal password window pops-up and accept any password you type, i thaught this will be a quick-fix…… but after accepting the password it takes you straight to “Preparing automatic repair” screen, and stucks there. Connecting the hdd via usb drive bay to desktop pc shows that the registry and regback is corrupt. There is no system restore files, User folder has two “new user” profiles. I backed-up the guys data, hdd back in notebook and tried to fix –
Access to the BIOS is available, but changes don’t “activate” anything… can’t boot from any other media than the Hdd. Onekey Recovery was the only option.
Did you disable UEFI Secure Boot before attempting to boot to other media?
Yes, in some weird way everything was blocked? Now that the Recovery is done it is possible to change boot media after disabling UEFI Secure Boot. I don’t know what the Indian guy did, and how long he had access to the notebook, the customer it seem went for a jog and left this guy “fixing” his pc – lol
This worked like a charm, thought I was going to have to start repairing the OS and hope I overwrote enough files to get in and still have this functional. Thanks for the help.
Thanks for the advice Steve. When I got the Access Denied message trying to get to System32 folder, I pulled the hard drive and connected to another computer via a USB Adapter. I was then able to navigate to the RegBack folder, and copied the five files to the config folder. After putting the dive back into the computer, Windows 7 booted normally, and everything seems to work just fine.
Thanks again
Thanks for the great info, first tried copying the on from the backup folders but didn’t work. Then copied the same ones with the .old extension and removed the .old and things worked great.
Thanks for the info.
Thank you so much. Read the review we posted. What a horrible feeling to fall for this scam and it helps to know you are not along. Our call came from
“POTS Phone 246-624-9999” We will try to report it. Thanks again. It really is like getting robbed, and I hope those HACKERS PAY dearly for all the damage they do. Karma baby!!!
Can you please tell me how to
Boot to external media of some sort (NOT your Windows installation) and navigate to the %SYSTEMROOT%\system32\config folder.
Where I can create a bootable media and how ?
One More question, If I re install windows 8.1 on my acer aspire notebook, it will work right ? although I lose my data but the problem will go away right ?
Thanks Steve. It worked a treat.
x
Not sure if it has been mentioned, but assuming the RegBack folder has not been tampered with this work just fine with windows 8. Great info.
I was able to unlock and log into a scammed Windows 8 laptop by booting an Ubuntu live CD and copying the RegBack files into place. THANK YOU! Please spread this link around! We did tons of reboots and password login attempts but copying RegBack files into place still let us log right in like normal. We had tried all the common passwords others had posted with no luck.
Be brave and go slow, you can fix it and spread awareness!!!
Follow this guide if you don’t know how to create and boot an Ubuntu live CD:
http://www.ubuntu.com/download/desktop/try-ubuntu-before-you-install
Once it is booted, you can explore your local disk disk using their file manager, and copy the files into place.
You could also yank the drive and manipulate the files on disk with another computer.
The support number they left on this computer is 1-844-278-0197
I had to work on a client’s computer today that had this scam perpetrated on it.
I was prepared to manually copy back the files but I tried the system restore first. There was only a system restore button on the startup screen in Windows 8 and it didn’t give me a choice of dates to restore to. It churned for about 10 minutes but when it came back, it was back to normal.
One thing I will add is it’s a good idea to make a full image backup of the computer. Programs like Acronis TrueImage and Macrium Reflect Free Edition can make a fully bootable image to an external drive. If your system is compromised, you can install a new drive or wipe your current drive, restore the image and boot up to exactly the way it was at the last backup time.
I tried copying the files in SYSTEMROOT%\system32\config\regback to SYSTEMROOT%\system32\config and that didn’t work. It’s still asking for a password. I can try it again but I expect the same thing to happen. Any other ideas?
Hey Michelle,
It’s probably because the system was rebooted too many times and the Regback entries were already replaced with the compromised/encrypted entries. Unless there’s another copy of the hives someplace or System Restore is still active, you unfortunately are probably looking at a data backup/reinstall.
-Steve
Im lost i cant even get into the laptop as obviously that password is there, when you say about doing that regback thing and having system root etc can u elaborate please as i dont understand it
Hey Rhys,
You have to boot to some sort of external media / another operating system first, or slave the drive to another working system. If you aren’t familiar with this sort of process you are MUCH safer bringing this to a professional to have it resolved. You can print my instructions and bring them to the tech and they should be able to have it resolved relatively quickly.
-Steve
This has just happened to me. I have wiped my computer to start again. Do you know if they can still access my computer.
@Joann:
I can’t say for sure as I haven’t been involved in the repair, but wiping and reinstalling removes all conventional software, including remote access software from the machine. So you should be all right if that’s the case.
Thank you so much man this was very helpful
Just wanted to say i ran into this here at my store and the regback was too new and had the encrypted SAM… i booted to hirens cd in XP mode… ran recuva on my c:\systemvolumeinformation and pulled out a good sam from the day before…
Interesting Robert, that’s a method I haven’t tried yet, though it makes sense if the SVI folder stores uncompressed/unobscured copies of the registry files. Thanks for the helpful information!
-Steve
Just wanted to share that the process shared here was spot on and worked like a charm. Very simple solution I must say. Only took a few minutes to carry out. For people looking for “bootable external media” take a look at this site. http://windowsmatters.com/2013/04/30/windows-8-based-pe-boot-disk-with-explorer-shell-and-all-my-favorite-apps/ Just a download of an ISO and burn do DVD. Very slick Windows 8 based PE boot disk loaded with a ton of utilities.
they called me from +919811308281.i just said its strange MS called me when im on Linux then they hang-up quickly
Hi
Excellent article, TY.
Now, for all of you REAL TECHs, have a look at:
http://www.scriptjunkie.us/2014/09/exploiting-ammyy-admin-developing-an-0day/
And exact revenge!!!
LOL. I can’t condone that… but it IS hilarious.
I saw this earlier this morning. What a funny way to turn the tables!
I’m a tech,but I hadn’t seen the scamming pricks lock it like this before.They got remote access to my customer but he got suspicious they were scamming him so he hung up but didnt call me till the next day,duh! They had all night connected to have a play.
Booted to a Live disc ,moved the reg hives around and bingo!
Cheers for the fix ,Superb work!
They used 12345m for the computer they stuffed for a friend and deleted all her files – was able to recover the files using free recovery software and simply reinstalled the OS – lesson learnt by young lady never believe random phone calls
We had a client with this EXACT situation. We had to pull the drive, copy her data and just do a system reset back to factory specs because she had rebooted several times before bringing it to us, and the VERY helpful article you wrote didn’t work. I wish we could prosecute these jackasses and sue for damages.
@CJ:
Yeah, must have already had the encrypted SAM copied over the backup. That’s a shame — but at least she got her data!
I had to respond and thank you for this solution! Fortunately the regback folder had not been cleared yet, and that fixed the problem completely! Fantastic.
India is the new Nigeria.
Some preventative workarounds before the fact. They may not help naïve users who may fall for this fraud, but technicians, computer suppliers, and tech-savvy friends can install them. They’re workable round by scammers, but they have to realise what’s happening:
1. Remove c:\windows\system32\syskey.exe. It’s pretty useless if you don’t intend to use it; you can keep a copy if you want. You can also create, in the same folder, a text file syskey.cmd which could display a message. I suggest “SAM on this computer has been locked against encryption. Enter your master password to enable encryption. Please contact your friend John Smith who set this up for you for more details” The script could then go into an infinite loop prompting for a “password”, responding “not recognised”, and asking again (a little knowledge of scripts and maybe a simple program required). Alternatively, a very visible message (flashing red?) “SCAM! SWITCH OFF! NOW!” (very visible at a glance, the scammer will close it ASAP), followed by “contact your friend …”. This may alert the scammer to lock the computer another way (I won’t say how), so the first variant might be better.
2. There’s a program called ERUNT which backs up the registry the first time the computer is started on any day, keeping by default the newest 30 backups. To restore, someone (the user or an expert consulted) boots with a Windows (not Ubuntu) boot disc (I use a BartPE) and follows a simple procedure explained in the ERUNT docs. (This is also useful to correct any sort of registry corruption, e.g., after a bad installation.) The ERUNT backups are of the registry only, not the huge System Restore backups. Obviously won’t repair other damage to files.
Two of my clients were hit in the last two days. Copying back the hive files worked for me via a Live CD. Thanks for your good work.
Just worked through this on my Gran’s laptop as she fell to the telephone malware scam a few weeks ago and it worked a bloody charm!
I just briefly installed her HDD in to my desktop, found the Sys32/config/regback files, replaced the ones in Sys32/config with the ones from regback. Now she doesn’t get this BS login screen. Thank you. 🙂
I just got this call! When the guy told me that iIn would need to pay $399 for a Lifetime Windows Installer ID and License ID for Windows Firewall, I got suspicious! I have deleted all of my temp internet files, cookies, history, etc. I re-booted my computer and disconnected it from my wireless internet. I turned the computer off. Now I am concerned that this guy will be able to get into my computer when I re-connect to the intrnet. Is there a way to know whether he has moved on to some other victim?
Did you ever let him connect to your PC remotely?
Thank you for your guidance. I was able to get a coworkers laptop back with your help. I was successful by doing the following procedure: Pull the compromised hard drive and hook up to another pc via USB to SATA Drive Adapter. Copy the SOFTWARE, SYSTEM, SAM, SECURITY, DEFAULT registry files from %SYSTEMROOT%\system32\config\RegBack folder and overwrite the same files in the %SYSTEMROOT%\system32\config folder. Reinstall the compromised hard drive back into original pc and power it up. Allow windows to do a repair operation and voila! Back in business.
worked fine for me – thanx for the advise
Thank you!
Your solution (copy back the data form RegBack) worked for me.
Most virus-removal / support-forums (at least in my native language where those scam calls are a younger phenomenon than in the US) are still clueless about this one and suggest tons of useless malware-scans and system recoveries.
I’m glad I found this.
This SCAM happened to me yesterday and I fixed it today, luck for me I was able to reset my computer to default settings.
I have a client who fell for the phone call scam not once, not twice, but 3 times! I hope he has learned his lesson. This time the used the syskey startup password thing. The client convinced the scammer to give him the password on the promise he would pay. The password was the client’s phone number, so try that (area code & number with no spaces or dashes). The restore points are all gone, so I was not able to re-copy the hives. The backup in the windows\system32\config\regback folder is 4 years old, so no help.
Hi there. Great explanation of this issue, but I am assuming this PC was rebooted making the hive repair worthless. The good thing is that the computer is fine if you just press enter at the password screen, I can access everything. However, we would still like to remove the password request when windows 8.1 boots. Is this possible? Also, can you take hive files from another source (Win 8 media or otherwise)? Thanks in advance for the help.
An idiot employee (19yo too!) at one of our stores fell for this scam after we left him alone for just 10 minutes! Scammer must’ve felt like he hit the jackpot when he discovered our computer wasn’t just an ordinary computer but one that contained valuable information. Anyways, after the comptuer was shipped to me to inspect it, I came upon this site then a few other sites. Ultimately, this method worked for me:
http://computernetworkingnotes.com/xp-tips-and-trick/remove-administrator-password.html
You create a boot CD and the website walks you through everything step by step (although I had to do the last part which was clear the admin password). Now I’m back into the system with all information intact. Whew!
Thanks this worked for me.
thanks worked like a charm
Thanks, worked perfectly!!
Thank you very much. Clear and helpful instructions that actually work.
Appreciate that this support is offered freely. A donation will be pending 🙂
Cheers
Had one of my customers hit with this. Instructions apply to Windows 8 as well, fortunately she still had a good Regback.
Note regarding trying system restore that I have found on Win8 – as the SAM is encrypted, it actually states you need to have an administrator to do the restore, and it couldn’t find any… (as the SAM is encrypted – DOH). Restore points had been wiped by them anyways…
So I unfortunately fell for the scam but my dad luckily did not give them his credit card info. Stupidly, I gave them access to our desktop though and they configured the account which led me to the startup thing with the password. I was able to restore the system and everything seems to be working fine..should I be worried about them getting passwords and such or did I stop them?
One of our customers had this prolem. Parents on holliday. Their son (alone at home) was so kindly to help Microsoft…… Anyway all data is now back. We performed the RegBack by connecting the harddisk via an externaldisk enlosure to the usb of a Laptop. It worked. THANKS!!!!
Worked like a charm! Thanks.
Thanks for this as this happened to me today & I have been locked out & felt smarmy about not paying until this bug appeared & prevented me from getting in..
AM currently in work & glad/optimistic I have found a solution & am not “the only victim”
I would say am not racist or narrow-minded & yes the person on the phone was Indian & very sneaky. Also after I said after being told you need to pay £39.99 for 5 year protection I protested & offered me a 1year for £19.99 & the 2nd man also Indian was even smoother until I hung-up
Nothing wrong with identifying a caller by their accent. “Racism” in that sense is part of compartmentalizing/categorizing the attacker, and there is absolutely nothing to be ashamed of in that.
The men speak with a thick Indian accent every single time I have encountered this scam, thus it is a critical profiling aspect. No need to apologize; this world has everyone on pins and needles when referencing nationalities, but it ought to be no different than a notation of hair color or eye color.
Hi. So, I got scammed and didn’t even know it. However, I can’t bypass the Startup Password. How do I begin there?
THANK YOU
Where are the Passwords stored so I can delete it. That should work. Because the alibaba deleted the back-up and the files in the %SYSTEMROOT%\system32\config
The ones in the %SYSTEMROOT%\system32\config\RegBack folder are still there but they were altered that day.
There has to be a way to just delete the password? I have the hard drive plugged into another computer and I can get into it now, so where are the passwords stored? Any help would be appreciated.
Actually there is. Are you running Windows 7 or before? If so, you can follow the instructions at this link (scroll down to “How to disable Syskey startup password”):
http://computernetworkingnotes.com/xp-tips-and-trick/remove-administrator-password.html
If it’s Windows 8, write me back and I’ll see if I can walk you through the procedure. I successfully completed it on a Windows 8.1 machine just the other day.
Also, credit to “FUScammers” on this find. It was my first attempt at actually removing the SAM password and I can confirm that it does in fact work with Windows 8.
We are recent victims of that “Start up password required” scam, too.
Windows 8.1
Dell XPS 8500
Tried to boot that download you recommended but unsuccessful at rebooting pooter.
We may be tech-challenged on “how to” do this.
Really would appreciate help!
Can they gain access just by calling and talking with you, or do you physically have to let them into your computer by following the steps they ask? or if your computer is on can they auto take over simply by it being on during your conversation, and how long does it take for them to have access?
Luckily for me the regback folder was there. I followed your instructions copying the files from the regback folder to the config folder and low and behold it worked!! Thank you so very much for sharing this info about how to do this. Nothing else i tried was working.
My grandmother was trying to download games on her computer and the website she went to told her that she needed an administrative password. They gave her a number to call and said that they were from bestbuy. She let then into her computer and now she said that there is this safe mode message that pops up and won’t let her on her computer. There is no message asking for a password. I’m going to check it out tomorrow to see if she’s just in safe mode or if they did something else. However, the person she spoke to was indian but it was a woman. Has anyone encountered this type of problem before? Someone did try to scam me but when they found out I was tech savy, they hung up.
I’m unclear of the instructions for Windows 8/8.1, can you help? I’d really appreciate it.
Thanks!
Actually the instructions should be the same. Let me know if you run into problems!
Hi, followed the steps to remove/disable syskey passwords on XP machine, it still prompts for admin and user passwords and setting them to blank does not help. Any advice?
Thank you
Another modus operandi also from a guy with thick Indian accent claiming to be calling from Windows support in the US, that the Windows license you’re currently using had been identified as being involved in cyber criminal activities and it will be deactivated. He’ll add that it may not be you as the same Windows license can some time be hijacked by other people, so he will offer you help to solve this problem and if you reject that then he’ll said it was indeed you who conducted the criminal activity and threatened to file charges against you. Don’t fall for it, no legit company will call up people about this kind of thing, just hang up and ignore the guy, don’t even entertain him with a conversation, unless if you want to play dumb and turn the scam on him!
Since being scammed I have noticed that I have had 5 caller’s saying a similar script. For a laugh 1 time I played along and after the 1st lady (who could hardly speak English) I was passed too an smoother sounding man who’s english was really good he tried to gain remote access and seemed angry after 17 mins. I kept or tried my best too keep him talking but he clicked I was wasting his time and hung up on me. & yes Indian every-time calling my mobile
I’d like to add my thanks to you for posting this valuable information. It allowed me to help a friend who had a foolish moment.
They are at it again. Now they claim your Windows license is expired and they show you (if you give them remote access) what information in your computer can be compromised; and for $200 they can renew your license. They are very slick….
Thanks for the Addendum advice; worked like a charm, had the machine fixed within minutes.
HELP! I’m stuck on the startup password thing. I can’t go passed it to do the next step.
Olá Pessoal estou agora com um cliente com o mesmo problema, em um Servidor com a configuração Windows Server 2012.
Porém tentei seguir os passos mas sem sucesso ao reinciar volta a janela de senha como antes, alguem passou por isso com um servidor ou ainda não temos solução para 2012 Server.
Hello everyone I’m going through this agora with a client with the same problem on a server with a configuration of Windows Server 2012 .
However I tried the Next Steps but without success . Reinciar back to the Password window as before, someone went through it with a server or we have no solution for Windows Server 2012 .
Thanks in advance!
Leonardo Gimenez
I picked up the phone asked who’s this and he answered my name is “Steve Smith” from microsoft support with an indian accent thats when i hung up and went to sleep hahaha but on another note try using these passwords before doing all these procedures they are very common : ari123
123 1234 123450 12345 123456 N123
Hello, I was unfortunately a victim of the indian scam and the only thing i could do was a complete system wipe since my keyboard and mouse didnt connect for some reason. The question itself is if it works to wipe the harddrive or if the syskey enacts upon every piece of hardware. Could buying a new harddrive solve it?
Thanks for the comments everyone!
Joel, no sweat; as syskey is merely an encryption of the SAM registry file specifically, even simply reinstalling Windows will solve the problem. No wife of the data is necessary, and no replacement of any hardware is required.
In Windows 8.1 & Windows 10 there is a very good option of resetting your computer to default settingsby going to advanced boot options reset your computer.
All the data will be lost however you will get your computer back.
Worked perfectly thanks. Downloaded the ISO and burnt it to a CD. Popped that into the laptop of the 80+ year old who had fallen for the scam and the password was removed. We were then able to restore to the previous day’s restore point. Lucky the laptop had a CD !
Unfortunately my mother-in-law fell for one of these scams. it was from a “tech” named Patrick Wilson with a thick Indian accent calling from 1-800-857-1898. He claimed he was affiliated with Microsoft and after charging her $99.95, actually sent her a receipt from Mea Solutions. I am trying to get her money back while spreading the word.
Many thanks. Unlocked syskey successfully. Windows was not then activated and called Microsoft to activate with no luck as there activation codes did not work. Followed this process and now fully up and running (old computer with Windows XP). https://community.spiceworks.com/how_to/3381-how-to-fix-windows-xp-activation-after-a-windows-xp-repair
First I want to say THANK YOU to everyone on this post for helping me past feeling like a complete dunce!!!! Now, I was scammed yesterday and I’m getting the infamous Startup Password screen….. I’ve read all the comments and I’ve tried the password 1234 once the screen boots and something happens……. Here’s where it gets interesting! My mother decided that since she gave me the laptop as a gift, I should be happy that it came on, even though I require an HDMI cord to use it because the screen is broken! Now anyone who is a tech knows immediately what my problem is……. All these solutions are great for someone who can see their screen, but I Sir Diddly Dumdum can’t, so I can’t do any of these things! I just want to know if there is a way to fix this or should I just chalk it up as a loss and buy a new computer?
I’ve read every thread, tried all passwords listed, and am stuck with win 8.1 on an HP 110-406 that will not allow backup through the system recovery program via cyberlink to DVD or external drive but I booted to Hiren’s and went straight to Mini XP but it doesn’t see the main drive, nor is the drive visible when removed, placed in a chassis and connected to other OS’s. Any ideas from other tools on Hiren’s or other distros?
I also am trying to recover from scam and syskey set on. However, I have Windows 10 and have tried an image file but the option to set the syskey did not come up.
Really struggling even tried to resore to previous point which still exist on the machine but it can’t install that correctly either.
If only there was an easy way, maybe the scammers are the people who sell the application that can sort it all out at a cost…
Huh , me to , same problem . I had backup of whole windows installation ,from before 3 weeks . Mounted in empty folder , copied whole NTUSER files from doc.setings.user.+ whole config folder from system 32 ,overwriten existing files and it WORKS !! Thanks a lot , ,
“I have Windows 10 and have tried an image file but the option to set the syskey did not come up.”
Not sure what this means exactly, however there is no reason to believe that the method I mentioned earlier to correct this in Windows 8 would not also work in Windows 10.
I can not thank you enough for the tutorial on how to pass through these crooks..yesterday I had one call me lock me out my laptop and keep calling asking for money..when I said I couldn’t pay they got rude and kept demanding money..when I hung up they kept calling back…well I came across this after a Google search and tried it and it worked..thank you..
The startup password is ALWAYS “1234” I have yet to see a scammer set it to something different
Thus far I have seen reports of:
ari123
123
1234
123450
12345
123456
N123
12345m
So they definitely vary it up from time to time.
Steve
Had this SCAM hit yesterday, and learned the hard way.. However I out scammed the scammer. When I had the password screen appear and they wanted their payment for their services I told them I can’t process a credit card online with out using my system. Gave me the password “WINDOWS123” which I wrote down. Told them to “F” off and hung up. Was able to have system open and changed the SYSKEY back to BLANK.
Everything fine now. Found out they want the funds to go to “Stanbic IBTC” a BANK in Nigeria!!
Have a Dell Laptop belonging to a friend which was on 8.1 but been upgraded to 10, and she has unwittingly been struck by these plonkers.
None of the above tricks have worked, and I’m looking for a way to get the machine to boot from the Recovery Partition, so I can cleanly reinstall windows 8.1 factory image.
Any pointers? I’m figuring it can’t be too hard, but it is a UEFI system (which I have imaged).
I really wish one of these jerks would call me. I’d troll them so hard. I’d make a virtual machine for them to mess with, with snapshots, and they’d hate me, I’d act dumb and then screw with them. I work in IT so i’ve seen this kind of scam.
Dear Steve, thank you so much for your article. Nearly 3 years after you posted it, it still does the trick, even with Windows 10. For those interested, here is the sequence of the actions that allowed me to unlock my sister’s PC (an ASUS N61J): 1°) I powered it on while pressing the key, to obtain the menu allowing me to boot on the CD-drive, where I inserted a DVD+R containing a bootable Linux Mint 17.2 Operating System; 2°) Inside Linux, I was able to copy the (unharmed) 5 files in scope from …system32/config/RegBack to …system32/config; 3°) Shutdown; 4°) Start the PC normally… —> back on tracks.
Just wanted to say thank you! My son’s teacher had this happen to them, I was all set to reinstall Windows but thought I’d check to see if I could find an easier workaround. Your regback trick did it, much less time consuming than having to reinstall everything!
So I just managed to get out of this scam with being able to do a system restore since I shut down my computer before they did too much damage. My question is should I have to worry about them having anymore access to my pc or having any malicious software left over? I already changed all my passwords and cancelled my card just in case.
Hey Daniel,
You should be ok as long as you restored to a date before they actually connected to your computer.
Steve
Thanks for the reply Steve one other thing I forgot to ask should I be concerned about identity theft since they got my full name and card details? I am unsure what else I should do. I have already alerted the bank/cancelled my card and changed all my passwords as I mentioned before, would it also be worth advising the police of potential identity fraud? I already submitted a report to “https://www.scamwatch.gov.au/” which is a federal site in Australia but I don’t know if I should bother contacting the police as well?
THANK YOU SO MUCH!! this actually worked fine for my friend’s pc.
I did have to overwrite the other files. this is a great knowledge base man!
@Daniel – You’ve done all you can. Cancelling the card and changing passwords should be plenty to keep them from trying anything more. (They are after the “low-hanging fruit” and likely won’t go to the trouble to do anything else with your info.) Don’t concern yourself with alerting the police. There is little to nothing they can do as these scammers cross international borders and no one will go after them since it’s so many little jobs… if you can even identify who they are.
I also have the box saying startup pass ward needed, now I got into the troubleshoot part of my laptop. I tried refresh & reset. I went to advance option where do I go from here? I am confused with this stuff?
I need help anybody out there? Please,,,, startup password problem
Hey Patricia,
If you are having trouble there is no safer advice than to have a professional solve this for you. I would recommend printing out my instructions here and handing them to the technician you choose. Explain to them that you would like for them to follow these directions to a T and they should have no issues if they are experienced.
One piece of advice: look for an independent, well-rated tech. It is not worth saving 50% on someone who’s terrible… and there are plenty of them. Likewise with the big-box stores; their feedback speaks for itself 🙂
Good luck,
Steve
I was just called in the same way. They make you focus on writing some numbers so you are not focused on the screen. Meanwhile they try to op syskey and change the password. I was able to stop him and disconnect the Remote Desktop program before he was able to do anything. I called my phone company to block them. I am not sure if anything is change so hopefully I can restart my pc without any problems.
Thank you so much! This was so helpful! Unfortunately I’m a tech at Staples so I don’t make shit for money, but I am bookmarking this page so I can donate as soon as I get a better job.
Will this work with Windows 10?
Yes, it has been confirmed to work with Windows 10.
Can this be removed via internal factory reset? I cannot see my screen because of it being cracked but I can naviagte to the factory reset well. Im locked out and my usual access to my screen is an external desktop screen. However to sensitive information windows locks out my external screen so I cannot see what Im doing.
Absolutely amazing find and post on this site!
This totally saved one of my co-workers Windows 10 All-in-one computers. The method of booting with a Linux Live CD and then copying the backed up files in RegBack to the config folder is what worked.
It was a little tricky because I had to disable SecureBoot first to get legacy boot devices and then I was enable to re-enable SB after and it booted up just fine. It’s too bad people fall for these scams though…
I can’t believe humans beings fall for cold callers…grrrrrrrrrrrrrrr
they will often use a really simple password like 123 or 123456. try passwords like that and if it works you can get back in and turn off syskey.
Hi,
Have a relative windows 7 PC that just got scammed. When i use the Addendum A boot cd i lot of text flies by and when i get to the loading SCSI it just stops there and never continues. Any thoughts?
Also anyone have have recent passwords? The ones above do not work.
So, I’ve run into this with a client using Windows 10.
I was able to disable syskey, but now the system boots like it’s going into Windows and restarts in a constant loop.
Anyone else experienced this? Suggestions?
Clean install is the last option and I’m trying not to go there yet.
Just used this article to successfully restore access to a Windows 10 Home x64 desktop. Luckily the system restore points had not been deleted so it was a relatively easy fix. Thanks so much for posting this great How To guide.
I had not encountered this vindictive twist to the tech support scam until today. The hardest part was persuading the computer to boot from another device (HP – Press Esc for options then F10 for BIOS. Change boot options to allow legacy boot.) Fortunately both the RegBack folder and the System Restore points had been left intact
Or you can delete the syskey program and let them try and tinker around. At that point, after they have found you don’t have it anymore, you can use the program they are using to connect to your computer and use the file transfer system in it and try to copy his files without him knowing, and then cut the connection and then remove the internet plug. Then call the police and give them the files or the FBI. Your choice in the matter since they might have to go through Interpol.
Here’s how to get rid of the syskey program and no, it won’t damage your computer even if it says it. It’s just getting rid of the program and nothing else.
1.) Go to your system32 file and search for syskey by searching in the search box.
2.) Right click and go to properties.
3.) Go to the security tab and click on advance.
4.) On the top, click on change and type administrator and then click on check names, if it says your user name/administrator and underlined, click on OK and then OK on the next window.
5.) Next, go to the Group or User Names: click on administrators, and then click on Edit.
6.) Check box Full Control and then apply and ok.
7.) Go to advance again and now look for Administrators and click on change permissions, click on administrators, Edit, Check mark full control and apply and then ok.
8.) That point, you can delete it as normally.
9.) Watch them suffer trying to use the program.
10.) Laugh like an evil Overlord
11.) Calm down and call FBI or Police, let them track your call and connections.
5.)
I had one of those guys call me, and I said where were you yesterday. He said yesterday? I said yes yesterday something happened to my computer and it caught fire burned and blew up. He hung up and I haven’t had any calls from them since.
I don’t use Windows but a few of us do what we can to help. I use Linux and VMware. I have a variety of Windows virtual machines and can easily run multiples with multiple configurations.
My phone number is also what was my business number. I am retired and have all the time in the world. I usually get from one to three calls in a month and have been for almost a year now. When I got the third or fourth one was when I set up the images.
It generally goes a bit like this…
They call and this nearly senile old man is suddenly hard of hearing. With enough prompting, I eventually get to installing TeamViewer, that seems to be their preferred virtual desktop sharing application. Then, I will eventually figure out the numbers and where they go. Of course, I will have had to boot the computer up in the first place.
You know us old folks, we aren’t that good with these newfangled computer boxes… (I was using them long before any of the callers were born.)
Then, sure enough, I will lose my Internet connection. Yeah, I live in the boondocks and that sure happens often out here. It is a fine time to tell them about my nonexistent grandchildren, seeing as the modem has to reboot.
Strangely enough, when I come back online, it has a slightly different configuration. That would be because it is a whole new image. Sometimes, they get even more greedy and I have them take a look at, “the missus’ computer.” Because, you know, they are already on the phone.
It is good wholesome entertainment, though the missus thinks I am crazy. I have had all sorts of fun with them. There is a nice KDE theme that looks just like Windows XP, that is always fun.
Sometimes, if I am really bored, I will allow scripts to run when I browse. Then I can see those fake ads that tell you your Windows computer is infected and to call this number to get help. I have more fun with them.
Anyhow, it is not my site so I will add that you can find screencast videos of a bunch of them on YouTube. There are a handful of folks who have fun with the scammers. If they were smarter, they would share numbers of bad marks because they aren’t going to be able to do anything with snapshot virtual images except for amuse me.
I figure they are paying for the calls and their time is taken up. So, I try to keep them on the phone for as long as possible. And no, my hearing is fine.
Now, this does absolutely nothing to help any of you. It isn’t meant to. Instead, I know how frustrating it is to have serious computer issues and I imagine that being scammed, on top of that, only makes it more infuriating. So, I figure you might as well get a chuckle knowing that they sometimes call a befuddled old man who isn’t so very good with that technology stuff, is nearly deaf, is rather absentminded, and has to take frequent bathroom breaks. My record is just a little shy of two hours, by the way.
There are a few of us that do this sort of thing and share the results. If more of us waste their time and make it unprofitable then we might get a few of them to quit. Oh, they won’t ever stop but we can certainly slow a few of them down and get a good laugh about it.
I do not want to spoil it for those who opt to go watch a video or two. Suffice to say, they eventually catch on and get irate. It is even more amusing when they aren’t catching on so you string them along for a while and then tell them that you are just screwing with them, that you are recording it, and that you will be uploading it to the web.
Retirement is not boring! 😉
I try to waste their time as much as possible also when they call me. Rarely am I in a position to sit down and load up a virtual machine, but I once kept a guy on the phone for nearly 45 minutes acting as though I was TRYING to allow him to connect!
It is absolutely hilarious.
-Steve
You are very much correct, it is absolutely hilarious. As they are snapshots of a virtual machine (I’ve been at this for about a year now) they can’t do any damage so I have no problem letting them connect.
They get mad… At me… As if I am the bad guy. I have no problem calling them back after they got angry and hung up. I called one back to inform him that he’d simply deleted all of my programs in a snapshot. He was livid and made a bunch of threats of physical violence and comments about my mother.
It was great fun and sometimes they will claim that they’re going to come to you and physically harm you. I am not the least bit concerned.
I prefer those who call me but that doesn’t happen often enough so I’m always excited to find a company that’s telling me that I have malware, throwing up a fake BSOD, and giving me a 1-800 number to call. They want to charge people $399 for a five year contract.
At best, absolute best, they’ll install CCleaner, AVG/Avast, and check your drivers. After you let them connect with TeamViewer, they run a script that shows a bunch of false positives – so it looks like you’re infected. They like to show things in the error log and claim those are major problems.
They go off a script and, for the most part, they seem to be using the same one – for the one where you call them up after your ‘error’ has popped up. They generally all say much the same thing until you get them going. They are also virtual fountains of knowledge, asking them technical questions is good for a laugh.
There will still be plenty left when it’s your turn to retire. It took me a few calls before I got into the swing of it but now I have my own script, sort of. I’m pretty sure that I’ve spoken to the same person more than once. I’m still not sure were they get the gall to be angry at me. That takes a certain something, I’m not even sure what it takes but I don’t think I could ever be that much of a jerk. They’re mad because I don’t let them steal from me… Go figure?
Anyhow, I try to keep them on the phone for as long as I can. I’m sure they are using VOIP so the calls are fairly cheap – but it is a toll-free number. I have no idea if they are paid on commission or hourly but wasting their time and costing them money keeps me amused for a little while.
So, there will still be plenty of scammers left when you hit retirement age. They are still calling and showing the fake errors so this scam must not be played out. Surely there’s something better to do with my time but that’s okay, I have plenty of time and everybody needs a hobby. There are a few of us that do this, some of them take it much more serious than I do.
I do not hold the record for call duration. One of us got about a four hour call AND they were able to string them along well enough so that they called back the following day. I’m pretty sure that’s the longest one that I know of. I figure if they’re stealing from people (and they are) then they’re fair game to target them for my own amusement. That and the longer they’re on the phone with one of us, the less likely they are to be stealing from one of your clients.
Hi Steve,
Many thanks for posting this article. With it I could regain access to my uncle’s Windows 10 computer.
Some other sites (one of which being the actual microsoft support site *shivers*) opted to try system restore or other Windows 10 recovery methods, all of which caused the affected machine to reboot at least a dozen times. In the meantime I did backup the Users folder.
Then I found your article and cursed at myself for not finding it earlier. Seeing as it is now september 11th I had no hope going to the RegBack folder… but was happily surprised to find their timestamps dating back to the 31th of august, before the attack on the 6th of september. I made an external backup of the RegBack files, then copied them into the folder above and rebooted.. No more password! Yay!
I checked Windows+R and the last commands are “eventvwr” and “www.warrantyeu.webs.com”. The first one probably convinced my uncle that the system had errors, and the website links to a TeamViewer setup download.. I better check what else they downloaded once they had remote access.
Thanks again for the article, really saved me a lot of time!
Cheers,
Mark
this just happend to me yesterday he called and i didnt know wat it was about and let him have control i reset it but i didnmt wipe all the drives should i do that please help
This happened to me today. I reformatted my laptop and changed all the passwords. Is my laptop safe for future usage lIke banking and buying online? Thanks a lot!
Thank you
Awesome….really like the retired guy who gives them a hard time!! Unfortunately they got my mom a couple weeks ago…. I’ll be trying this out, they pretty much blocked everything to easily rid the sys password!! Thanks a million!!
Hi,
Does anyone know if the Addendum A method works on Windows 10? I checked and they managed to clear all of my restore points and the computer has been restarted so I’m not sure if the first method would work at this point. I’d like to try the Addendum A method but I just want to make sure that it should work on 10 before I try. Thanks!
Hey Matthew,
I do believe that it normally also works on Windows 10. However, much like 8, you will likely need to copy the registry hives to a supported partition/filesystem type first (FAT32/NTFS on an MBR formatted disk, such as a USB flash drive) before the modifications take place. Afterwards they can be manually copied back to the affected machine’s system32\config folder.
Hope this helps.
Steve
So I would have to manually go to the regback folder and copy those files over to a USB drive? If windows created a new regback copy does that mean there is nothing I can do? Also will I be able to copy those files by booting to the same file that the Addendum suggests to download or will I need to boot to another cd first. Sorry for having so many questions, I just want to know exactly what I’m doing before I do it.
Good Day,
I have tried this method and no joy. Went with the boot from the samreset.iso disk (linux) and removed the syskey password. Have rebooted and I no longer get that Startup Password pop-up ,but the computer does not boot either. Tried going in through the CMD and copying over the \RegBack files to the config. Still no joy.
I have spend three nights over the last three weeks tyring to fix my sisters computer. She updated to Windows 10 the last week it was free but did not do a rescue/recovery disk after the install. She is using my traveling laptop but I would really like to get this fixed for her. Any suggestions?
Thank you for any assistance.
Mark
Hello,
I tried this fix to no avail, those old registry files in system32 must be bad. I was able to get through the password a couple times before I figured out this was a SAM hive hack, and that must have screwed me.
Thing is, the attack seems more sophisticated. I can’t even hit F8 or any other F key from boot, it goes so damn fast to the password. The password itself changes each time I try. External media won’t work.
At this point my friend (who’s computer it is) doesn’t care if the HD is wiped. I have a USB to reinstall windows but obviously can’t even do that right now.
What can I do? Any articles you can please point me to? I’m at a loss, tried a million things.
Hey there,
Most likely the reason you are unable to press F8 to reach the Advanced Boot Options menu is that it does not exist in later versions of Windows; and plus, if you are booting UEFI Secure Boot, the sequence is so quick that you have very little time to intervene anyway. You’ll need to boot to external media anyway to correct the problem, which involves reaching BIOS, not the F8 boot menu. It wouldn’t do you any good to reach Safe Mode anyway!
-Steve
Mark,
Not sure — sounds to me like some sort of configuration inconsistency however (restoring old hives should have worked). You may be able to reach the Recovery Environment and invoke an offline System Restore now that the startup password has been removed.
-Steve
Steve,
I have a USB drive that is set up for windows install, but with it plugged in I cannot get to boot to that. No way to access BIOS, as the PW comes up so quick. Am I missing something?
Thanks!
Is this some sort of exotic laptop model, such as a Lenovo Yoga or similar?
Steve
Steve,
No it is an Asus F551C.
I have no ability to boot from the USB that I can figure.
Thanks again
http://www.asus.com/US/support/FAQ/1008829
Unfortunately, no dice. I don’t even get that initial quick “Asus” logo screen. Just straight to the password.
I think this hack has gotten a bit tougher, or the setup on Asus PC’s makes it more potent.
Thing is, that’s not technically possible. Plus — and trust me on this — these hacks are not sophisticated enough to implement BIOS-level lockouts remotely. What MUST be happening in your case is that the machine is not shutting all the way off, but rather is merely sleep/resuming. In light of this:
1. Press the power button and release to turn on the machine, then IMMEDIATELY (1 second later as the machine is powering on still):
2. Press and HOLD the power button for AT LEAST five seconds until the machine completely and totally powers off.
3. Then, after this, follow the instructions to enter the BIOS on that page.
Steve
Yup, still nothing. They are in the BIOS I’m pretty sure.
More information – I booted without the hard drive in and the USB windows install plugged in. Still a password, can’t get past it.
Tried powering completely down, removing battery, etc. Then trying to F2 then power as the instructions show. Absolutely no dice.
Ok, I know what it is. I hate to tell you this, but this is an Asus laptop issue. I have dealt with it in the past. The problem is that the machine recalls that the OS is in a suspended state and mistakenly refuses to allow any preboot operations (namely, BIOS access) to occur. It is probably an attempt to expedite resume processes after hibernation.
Sadly, there is only one fix I know of: to boot the machine and gracefully shut it down, which you likely cannot do thanks to the startup password. That would mean you would need to remove the hard drive and install one with an unlocked OS, boot, then shut it down to remove the flag from the BIOS memory which is skipping the F2 keypress check. Yep, that’s right: as insane as it sounds, that’s the issue. It is a known problem.
I’m not sure if later BIOS updates correct this, but they might. Regardless, the point is the same: you will probably need to physically remove the drive from the system, unless Asus knows another way. And while it’s out, you might as well just hook it up to another machine and copy over the registry hive files as detailed in my original blog post. Or, you can run the addendum A procedure to ensure you correct it on the first go.
Good luck!
Steve
Here is a similar example by the way which illustrates the same problem:
http://superuser.com/questions/395871/after-windows-8-installation-i-cant-access-bios-settings-anymore
Steve
Steve,
Thanks again for the response. That really explains a lot. Sorry for my delay, I haven’t had a chance to try and address this yet.
I did try the copy over of the registry hive files earlier without success. I plan to get a hold of a hard drive with a fresh install and reset the state of the laptop with a good boot up, and then reformat the original drive so I can boot from USB and do a fresh windows install.
I will try to follow up with any successes. This has really become a much more annoying issue than I thought it would be!
What is the best iso to use, and then best way to burn to a USB I tried samreset and when I chose 1 nothing happens and cannot get to see my files, this is Windows 10, my MIL talked with them on the phone and I am stuck
I mentioned earlier that with 8/8.1/10, you must copy the registry hive files manually to a FAT32 formatted disk from the UEFI/GPT partitioned disk so that you can access the files with samreset (which is not GPT partition type aware). After the resetting procedure is completed on the hives, you can then safely copy them back to the Windows\system32\config folder to facilitate the boot.
Hope this helps.
Steve
I thought I was sort of technical but how do I copy manually if I cannot get in, I just used Linux iso and when I click under devices and OS , I get a huge error error mounting. I am willing to try anything before I reformat
Appreciate the help
When I try to access the OS from Linux, I get this error;
Error mounting /dev/sda3 at /media/mint/OS: Command-line `mount -t “ntfs” -o “uhelper=udisks2,nodev,nosuid,uid=999,gid=999” “/dev/sda3” “/media/mint/OS”‘ exited with non-zero exit status 14: The disk contains an unclean file system (0, 0).
Metadata kept in Windows cache, refused to mount.
Failed to mount ‘/dev/sda3’: Operation not permitted
The NTFS partition is in an unsafe state. Please resume and shutdown
Windows fully (no hibernation or fast restarting), or mount the volume
read-only with the ‘ro’ mount option.
Looks like I rebooted too many times as I still get the error. Can I copy those 5 files from another Win 10 instance and copy them in Config? Anything else I can try?
Hey Mike,
Nope, they’re extremely specific to your machine. At this point, if you can’t get the samreset boot disk to work, I’m afraid you’ll have to either take it to a tech who can or just back up your data and reinstall.
Steve
Steve,
Finally acquired a drive with a good windows version. Replaced the original HD with the new one, same issue. I can’t boot up, it goes straight to the password. It must be locked in on the MOBO?
It may be that I need a new MOBO, and therefore likely just a whole new laptop given the cost?
Hey B,
Well, that’s just nuts. There’s about a zero percent chance (roughly) that this was provoked by the attackers. Instead, it’s almost certainly an issue with the board as we discussed… unfortunately, it seems only ASUS may be able to provide the answer. Historically I have seen these sorts of issues with their devices in the past, so it wouldn’t be the first time I ran into something really odd in the way of firmware from them.
I really hope you get this sorted out. If you do, please do report back and let us all know how you did!
Steve
Hi there.
It happened to me. unfortunately.
I’m in the stage that required a startup password.
And from this it goes directly to restart and then a have the blue screen.
What can I do?
Pleas I need help.
Thank You, just saved a ton of time fixing a clients computer after she got scammed.
Thanks! The PC I was fixing had the RegBack folder still intact, so was just a matter of copying it over the encrypted hives and voila! Back in action.
This worked perfectly. I had a REGBACK folder. Saved my client
FYI – I just used 123456 on my client’s laptop and was able to get in.
Hi I have done the Windows defender offline and it asks for my start up password when it is finished. I put it in the request came back up so I put it up again. Then it seems to accept it but it goes back to the loading screen like it will actually start but underneath it says preparing automatic repair. No matter what I do it does it again and continues to redo the Windows defender offline scan again. Also I am using the internal software for it. Just selected it from the section for security. It won’t even let me sign on to the actual computer. HELP.
Thanks Lot.
It worked . I used the Advanced Options to copy the back up Reg files
Backup the registry hives in this folder to a temporary location. The files are:
SOFTWARE
SYSTEM
SAM
SECURITY
DEFAULT
Navigate to %SYSTEMROOT%\system32\config\RegBack as mentioned earlier.
Copy all registry hives from this folder (the same files as listed above) into the %SYSTEMROOT%\system32\config folder.
Reboot the PC.
I received a similar call just now, as well!
I”m not 100% familiar the inner workings or Windows, but know enough when the guy is getting me places I don’t want to be.
I only wasted about 15 minutes of his time, slowly booting up the PC (it was booted, but he thinks it took about 2 minutes), then slowly mis-typing and re-typing his instructions. In this case, he asked me to use the RUN command to go to http://www.11gb.net.
Given the amount of time I already wasted on him, and that I really did have to get going, he offered to call me back another time. IF he calls, and I can afford to take more of his time (such as putting away groceries, as I was), I’ll say getting him to cuss at me would be a successful interaction.
YES, be careful if you don’t know what you’re changing. Never make any changes or give control over. Best thing, say something about being a lying XXXX and hang up on him. 😉
Dang they got me and I can’t get into my pc . Can anyone help
Had this happen to a friend’s PC with Win10. Anything that can be done if the RegBack files are gone? Thanks in advance
Just experienced some scammer posting their phone number as major company out there. When one call they will pretend to be them and ask for remote assistant.
FYI, if you are on Windows 8 or 10 just boot using recovery tool and boot into dos. regardless just follow steps 4 to 6
but with some change. check %SYSTEMROOT%\system32\config\RegBack to see if you have
SOFTWARE
SYSTEM
SAM
SECURITY
DEFAULT
if you do
go to %SYSTEMROOT%\system32\config
and delete (the following file should have a modified date time of then the scamer got to your machine)
SOFTWARE
SYSTEM
SAM
SECURITY
DEFAULT
copy %SYSTEMROOT%\system32\config\RegBack
SOFTWARE
SYSTEM
SAM
SECURITY
DEFAULT
to
%SYSTEMROOT%\system32\config folder.
Reboot the PC.
This solution works! I got same spam yesterday from spammer. The regback is present, after removing infected, everything works OK.
Any way to not allow Syskey to be used before this sort of thing happens? I’m thinking about disabling it on some relatives computers so that it can’t be used if they fall for the scam.
Thank you so much, it worked with Koe’s explanation for Windows 10
Simple way to avoid this problem in the first place: DON’T ALLOW REGULAR USERS TO USE THE COMPUTER WITH LOCAL ADMINISTRATOR PRIVILEGES! This is basic computer security principle that everyone seems to ignore. If the regular user had restricted user rights then any attempt by the Indian scammer to run syskey.exe, even thru a remote desktop session, would have kicked up a UAC prompt for the administrator’s account name and password. Once you save the user’s computer using the backup registry keys, also advise them to set up a separate superuser account and password, and demote their regular account to “standard user”. That is, if you’re a honest computer tech, else you know they’re gonna be repeat customers in the future!
Can I get a number of someone who can help me remove Syskey from my laptop
The very first suggestion works! Even in Windows 10. Thank you
“POWER OFF your PC immediately.
Boot to external media of some sort (NOT your Windows installation) and navigate to the %SYSTEMROOT%\system32\config folder.
Backup the registry hives in this folder to a temporary location. The files are:
SOFTWARE
SYSTEM
SAM
SECURITY
DEFAULT
Navigate to %SYSTEMROOT%\system32\config\RegBack as mentioned earlier.
Copy all registry hives from this folder (the same files as listed above) into the %SYSTEMROOT%\system32\config folder.
Reboot the PC.”
“POWER OFF your PC immediately.
Boot to external media of some sort (NOT your Windows installation) and navigate to the %SYSTEMROOT%\system32\config folder.
Backup the registry hives in this folder to a temporary location. The files are:
SOFTWARE
SYSTEM
SAM
SECURITY
DEFAULT
Navigate to %SYSTEMROOT%\system32\config\RegBack as mentioned earlier.
Copy all registry hives from this folder (the same files as listed above) into the %SYSTEMROOT%\system32\config folder.
Reboot the PC.”
This worked for me brilliantly.
Embarrassed to have to admit I fell in such trap when I always previously used to hang up in those fraudulent calls. But the above worked for me brilliantly. many thanks
This is the best solution post ever!!! I saved the reg backups earlier in my quest to restore the system. It made this so easy.
Hi Steve
I just got scammed and was hoping that you could help me with the syskey password
Hello,
Friend of mine was scammed, I was able to follow the post proposed resolution. Three machines with Windows 10 worked as a charm. No need for the cracking of the password, just used RegBack files. I am in Amarillo, TX if anyone needs help, try to reach me at snyrkov@gmail.com
This happened to me, except my computer was freezed and I had to call a number for it to be fixed and they charged me 150 and he kept trying to persuade me. He connected to my computer and I couldn’t pay, but he continued to try to get me to pay but I ended the connecting session and ended the call. I’m not sure if this was a scam or not, but I now cannot use my computer.
The “freeze” was merely a popup dialog box from a scam website — it’s not even a computer problem. You can escape the box by either killing the browser process from Task Manager, or even easier, shutting down/restarting by clicking the Start button.
Calling the number that the scam site generates is when the trouble starts!
A relative had a question about a Brother printer problem and googled looking for a phone number. Called 844-888-3870 (I think) and the person who answered said they could solve the problem. Remote access was granted to the machine and that’s when this ransom problem started for them.
Lesson learned: 1)never grant remote access to your machine
2) don’t believe everything you see in google.
I fault Brother for not publishing their phone number and Google for allowing these ads that lead to scams like this.
Thanks!!!!
Replacing registry files from RegBack worked even after trying to boot by guessing password several times!!!
My laptop was locked up by the same India men. They put a start-up password on it because I did not have the 250.00 to pay them . After days if trying to get them back on the phone to get them to unlock my laptop , I was able to scam them. I called them from a new number and told the. I needed their help repairing my laptop. I earned his trust and said I was desperate to have my laptop fixed. No worries he says. I said I can’t get past the startuo password. He said try ” qwerty123 the first five keys on a key board and 123 to unlock it. It worked so I said wait a minute and hung up then had to block his number. Lol haha so if you have your stuff locked by the thieves the code is qwerty123 to get back in.
They must have updated the password….Same thing happened here and this code does not work :-f Completely locked out of desktop…
They hardly ever use the same password; there are very, very many scam organizations out there performing these hijacks. That’s the point of this article: to get you back in since it truly isn’t usually as simple as just guessing a premade password.
-Steve
My windows 10 computer was havked and now I can’t get back in it.
I try to turn it on and it says administrator password is deleted or doesn’t exist. I can’t log onto internet with Ethernet. My hotspot, or Bluetooth.ive tried everything.. the computer is only a month old..PLEASE HELP